Towards IT-Legal Framework for Cloud Computing
As the common understanding of Cloud Computing is continuously evolving, the terminology and concepts used to define it often need clarifying. Therefore, Cloud customers and Cloud Providers are used to dispute about Service Level Agreements, Service Level Objectives and Quality of Service. Simultaneously, SLAs/SLOs/QoS represent other related technical problems such as Security, Privacy, Compliancy and others. Technical problems are usually defined within technical context, where both parties ignore analyzing problem's legally related causes. In fact, these problems are stemming from the
Traffisense: A smart integrated visual sensing system for traffic monitoring
Intelligent camera systems provide an effective solution for road traffic monitoring with traffic stream characteristics, such as volumes and densities, continuously computed and relayed to control stations. However, developing a functional vision-based traffic monitoring system is a complex task that entails the creation of appropriate visual sensing platforms with on-board visual analytics algorithms, integration of versatile technologies for data provision and stream management, and development of data visualization techniques suitable for end-users. This paper describes TraffiSense, a
An approach for extracting and disambiguating arabic persons' names using clustered dictionaries and scored patterns
Building a system to extract Arabic named entities is a complex task due to the ambiguity and structure of Arabic text. Previous approaches that have tackled the problem of Arabic named entity recognition relied heavily on Arabic parsers and taggers combined with a huge set of gazetteers and sometimes large training sets to solve the ambiguity problem. But while these approaches are applicable to modern standard Arabic (MSA) text, they cannot handle colloquial Arabic. With the rapid increase in online social media usage by Arabic speakers, it is important to build an Arabic named entity
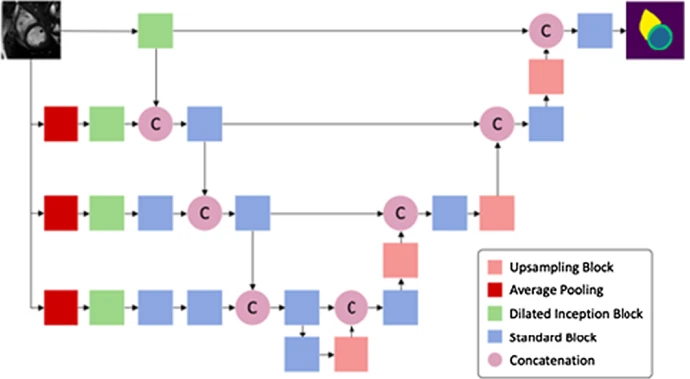
Multi-center, Multi-vendor, and Multi-disease Cardiac Image Segmentation Using Scale-Independent Multi-gate UNET
Heart segmentation in Cardiac MRI images is a fundamental step to quantify myocardium global function. In this paper, we introduce a pipeline for heart localization and segmentation that is fast and robust even in the apical slices that have small myocardium. Also, we propose an enhancement to the popular U-Net architecture for segmentation. The proposed method utilizes the aggregation of different feature scales from the image by using the inception block along with the multi-gate block that propagates the multi-scale context of the supplied data where the heart is subject to changes in scale
Combined regional and spatio-temporal approach improves hepatic tumors classification in Multiphase CT
In this work, we investigate the effect of using spatio-tepmoral features on a regional basis on the liver focal lesions classification performance in the multiphase CT images. Texture, Density, and temporal feature set and their different combinations along spatial partitioned ROI were investigated to better characterizing five hepatic pathologies from multiphase contrast-enhanced CT scans. Embedded feature selection followed by decision tree ensembles classification with ten folds cross-validation were employed to classify a total of 180 ROI includes normal tissues, cyst, haemangioma
Features selection for building an early diagnosis machine learning model for Parkinson's disease
In this work, different approaches were evaluated to optimize building machine learning classification models for the early diagnosis of the Parkinson disease. The goal was to sort the medical measurements and select the most relevant parameters to build a faster and more accurate model using feature selection techniques. Decreasing the number of features to build a model could lead to more efficient machine learning algorithm and help doctors to focus on what are the most important measurements to take into account. For feature selection we compared the Filter and Wrapper techniques. Then we
Controlled alternate quantum walks based privacy preserving healthcare images in Internet of Things
The development of quantum computers and quantum algorithms conveys a challenging scenario for several cryptographic protocols due to the mathematical scaffolding upon which those protocols have been built. Quantum walks constitute a universal quantum computational model which is widely used in various fields, including quantum algorithms and cryptography. Quantum walks can be utilized as a powerful tool for the development of modern chaos-based cryptographic applications due to their nonlinear dynamical behavior and high sensitivity to initial conditions. In this paper, we propose new
Extreme Points Derived Confidence Map as a Cue for Class-Agnostic Interactive Segmentation Using Deep Neural Network
To automate the process of segmenting an anatomy of interest, we can learn a model from previously annotated data. The learning-based approach uses annotations to train a model that tries to emulate the expert labeling on a new data set. While tremendous progress has been made using such approaches, labeling of medical images remains a time-consuming and expensive task. In this paper, we evaluate the utility of extreme points in learning to segment. Specifically, we propose a novel approach to compute a confidence map from extreme points that quantitatively encodes the priors derived from
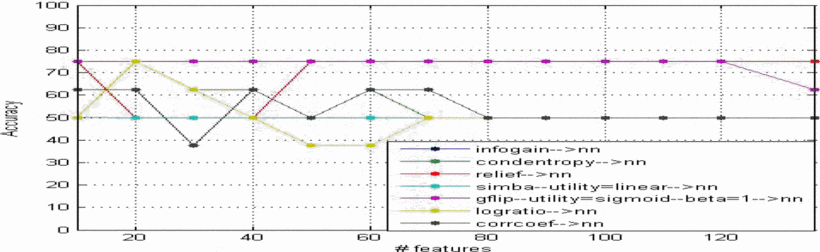
Feature selection in computer aided diagnostic system for microcalcification detection in digital mammograms
In this paper an approach is proposed to develop a computer-aided diagnosis (CAD) system that can be very helpful for radiologist in diagnosing microcalcifications' patterns in digitized mammograms earlier and faster than typical screening programs and showed the efficiency of feature selection on the CAD system. The proposed method has been implemented in four stages: (a) the region of interest (ROI) selection of 32x32 pixels size which identifies clusters of microcalcifications, (b) the feature extraction stage is based on the wavelet decomposition of locally processed image (region of
Towards scalable and cost-aware bioinformatics workflow execution in the cloud - Recent advances to the tavaxy workflow system
Cloud-based scientific workflow systems can play an important role in the development of cost effective bioinformatics analysis applications. So far, most efforts for supporting cloud computing in such workflow systems have focused on simply porting them to the cloud environment. The next due steps are to optimize these systems to exploit the advantages of the cloud computing model, basically in terms of managing resource elasticity and the associated business model. In this paper, we introduce new advancements in designing scalable and cost-effective workflows in the cloud using the Tavaxy
Pagination
- Previous page ‹‹
- Page 10
- Next page ››
