Named entity recognition of persons' names in Arabic tweets
The rise in Arabic usage within various socialmedia platforms, and notably in Twitter, has led to a growing interest in building ArabicNatural Language Processing (NLP) applications capable of dealing with informal colloquialArabic, as it is the most commonly used form of Arabic in social media. The uniquecharacteristics of the Arabic language make the extraction of Arabic named entities achallenging task, to which, the nature of tweets adds new dimensions. The majority ofprevious research done on Arabic NER focused on extracting entities from the formallanguage, namely Modern Standard Arabic
Streaming support for data intensive cloud-based sequence analysis
Cloud computing provides a promising solution to the genomics data deluge problem resulting from the advent of next-generation sequencing (NGS) technology. Based on the concepts of "resources-on-demand" and "pay-as-you-go", scientists with no or limited infrastructure can have access to scalable and cost-effective computational resources. However, the large size of NGS data causes a significant data transfer latency from the client's site to the cloud, which presents a bottleneck for using cloud computing services. In this paper, we provide a streaming-based scheme to overcome this problem
New governance framework to secure cloud computing
Cloud computing is enabling proper, on-demand network access to a shared pool of computing resources that is elastic in reserve and release with minimal interaction from cloud service provider. As cloud gains maturity, cloud service providers are becoming more competitive, which increase the percentage of cloud adoption. But security remains the most cited challenge in Cloud. So, while we are progressing in cloud adoption, we have to define key elements of our cloud strategy and governance. Governance is about applying policies relating to used services. Therefore, it has to include the
Towards Efficient Online Topic Detection through Automated Bursty Feature Detection from Arabic Twitter Streams
Detecting trending topics or events from Twitter is an active research area. The first step in detecting such topics focuses on efficiently capturing textual features that exhibit an unusual high rate of appearance during a specific timeframe. Previous work in this area has resulted in coining the term "detecting bursty features" to refer to this step. In this paper, TFIDF, entropy, and stream chunking are adapted to investigate a new technique for detecting bursty features from an Arabic Twitter stream. Experimental results comparing bursty features extracted from Twitter streams, to Twitter
Transform domain two dimensional and diagonal modular principal component analysis for facial recognition employing different windowing techniques
Spatial domain facial recognition Modular IMage Principal Component Analysis (MIMPCA) has an improved recognition rate compared to the conventional PCA. In the MPCA, face images are divided into smaller sub-images and the PCA approach is applied to each of these sub-images. In this work, the Transform Domain implementation of MPCA is presented. The facial image has two representations. The Two Dimensional MPCA (TD-2D-MPCA) and the Diagonal matrix MPCA (TD-Dia-MPCA). The sub-images are processed using both non-overlapping and overlapping windows. All the test results, for noise free and noisy
Towards IT-Legal Framework for Cloud Computing
As the common understanding of Cloud Computing is continuously evolving, the terminology and concepts used to define it often need clarifying. Therefore, Cloud customers and Cloud Providers are used to dispute about Service Level Agreements, Service Level Objectives and Quality of Service. Simultaneously, SLAs/SLOs/QoS represent other related technical problems such as Security, Privacy, Compliancy and others. Technical problems are usually defined within technical context, where both parties ignore analyzing problem's legally related causes. In fact, these problems are stemming from the
Traffisense: A smart integrated visual sensing system for traffic monitoring
Intelligent camera systems provide an effective solution for road traffic monitoring with traffic stream characteristics, such as volumes and densities, continuously computed and relayed to control stations. However, developing a functional vision-based traffic monitoring system is a complex task that entails the creation of appropriate visual sensing platforms with on-board visual analytics algorithms, integration of versatile technologies for data provision and stream management, and development of data visualization techniques suitable for end-users. This paper describes TraffiSense, a
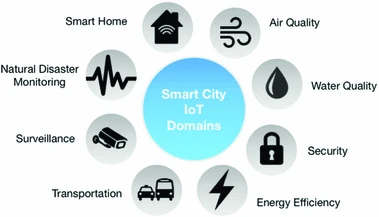
A survey on smart cities’ IoT
The rise of the Internet of Things (IoT) has led to a numerous and diverse amount of products and real life implementations for smart cities in the last few years. With the many opportunities and challenges, the academic and industrial field has come up with many hardware and middleware platforms. We categorise these different IoT applications and solutions into different domains and present an application for each. This survey aims at defining the state-of-the-art major and common technologies, frameworks, and applications used to open doors to drive future research and to spark new ideas for
Health Records Privacy Issues in Cloud Computing
Personal health record service avail patients to store and dominate their healthy information data through the cloud. Many users like medical doctors, health care providers and family members can access this data through the internet. However, there are privacy issues related to data exposure and data breaches, causing risk to patients' lives. Encryption techniques like public key encryption are applied but they are not efficient and very complex, in addition to scalability problems. In this paper, various multi-authority attributes based on encryption solutions features are discussed that
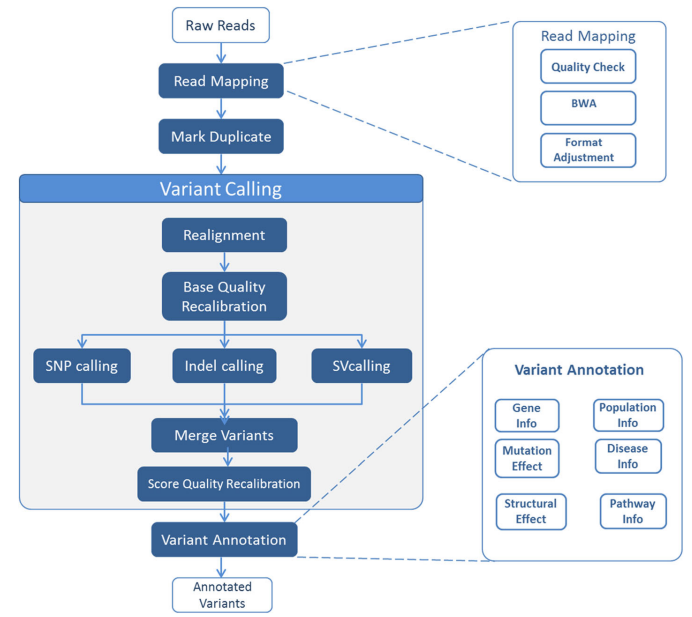
MC-GenomeKey: A multicloud system for the detection and annotation of genomic variants
Background: Next Generation Genome sequencing techniques became affordable for massive sequencing efforts devoted to clinical characterization of human diseases. However, the cost of providing cloud-based data analysis of the mounting datasets remains a concerning bottleneck for providing cost-effective clinical services. To address this computational problem, it is important to optimize the variant analysis workflow and the used analysis tools to reduce the overall computational processing time, and concomitantly reduce the processing cost. Furthermore, it is important to capitalize on the
Pagination
- Previous page ‹‹
- Page 43
- Next page ››
