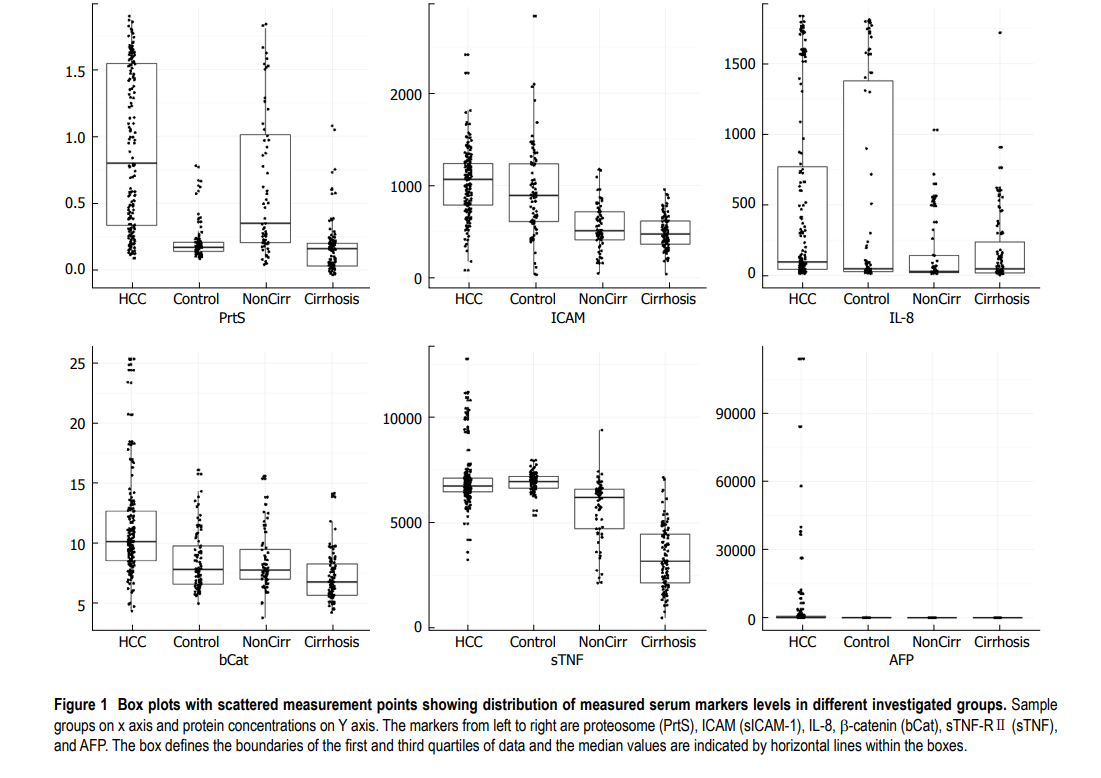
Early detection of hepatocellular carcinoma co-occurring with hepatitis C virus infection: A mathematical model
AIM: To develop a mathematical model for the early detection of hepatocellular carcinoma (HCC) with a panel of serum proteins in combination with α-fetoprotein (AFP). METHODS: Serum levels of interleukin (IL)-8, soluble intercellular adhesion molecule-1 (sICAM-1), soluble tumor necrosis factor receptor II (sTNF-R II), proteasome, and β-catenin were measured in 479 subjects categorized into four groups: (1) HCC concurrent with hepatitis C virus (HCV) infection (n = 192); (2) HCV related liver cirrhosis (LC) (n = 96); (3) Chronic hepatitis C (CHC) (n = 96); and (4) Healthy controls (n = 95). The
Decoding arm kinematics from EMG signals using Kalman filter
Myoelectric control of prosthetic arms provides a new hope for providing naturalistic movements to amputees. Extensive work has been made in recent years to use Electromyography (EMG) signals to enhance the operation of prosthetic arms. In this paper, we propose an EMG Kalman filter-based model, where we identify the relationship between the joint angles and recorded EMG signals. EMG signals were recorded from biceps and triceps muscles and used to train a Kalman filter decoder. We assessed the performance of the decoder by computing the correlation and the normalized root mean-square error
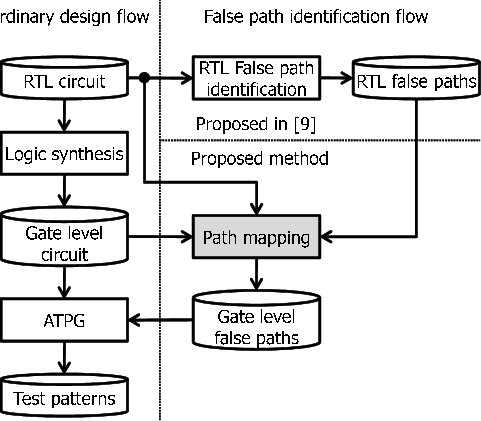
Utilization of Machine Learning In RTL-GL Signals Correlation
Verification is an important part of the Electronic Design Automation (EDA) design flow which currently takes a considerable amount of time. During the synthesis process, Different optimizations are done to the Register-Transfer-Level (RTL) code to optimize the power, area, and speed of the circuit. These optimizations result in changes in the names of signals at the gate level. Automatic signal mapping can improve the verification process and can be used to guide functional verification activities between the two presentations using (Clock domain crossing (CDC) analysis in RTL, Gate Level CDC
The H3ABioNet helpdesk: An online bioinformatics resource, enhancing Africa's capacity for genomics research
Background: Currently, formal mechanisms for bioinformatics support are limited. The H3Africa Bioinformatics Network has implemented a public and freely available Helpdesk (HD), which provides generic bioinformatics support to researchers through an online ticketing platform. The following article reports on the H3ABioNet HD (H3A-HD)'s development, outlining its design, management, usage and evaluation framework, as well as the lessons learned through implementation. Results: The H3A-HD evaluated using automatically generated usage logs, user feedback and qualitative ticket evaluation

Securing Hardware from Malicious Attacks
Hardware security is considered a major design and manufacturing target area with a broad range of research and development topics such as protection of intellectual property (IP), metering of hardware, detection of hardware Trojans, and a lot of other topics. This paper discusses Trojan realization in integrated circuits (ICs), as well as the possible security measures, also exploring the usage of the 3-D integration in hardware security where additional hardware can be mounted after fabrication to foster secure execution just for those systems which need it. © 2021 IEEE.
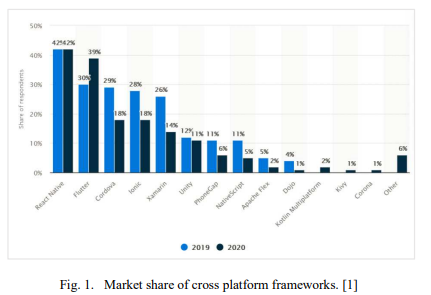
General Trans-Compiler based Mobile Applications Converter
Deployment on different platforms has been a great issue for mobile companies that aim to maximize the return on investments by making their mobile applications available on different mobile platforms. Consequently, the app may be developed several times to match different platforms. Therefore, there is a need to have solutions that enable the developers to develop the app once, and run it everywhere to reduce the cost of development and reach out to maximum users across several platforms. In this paper a tool is provided with the most popular languages /frameworks (native, cross platform)
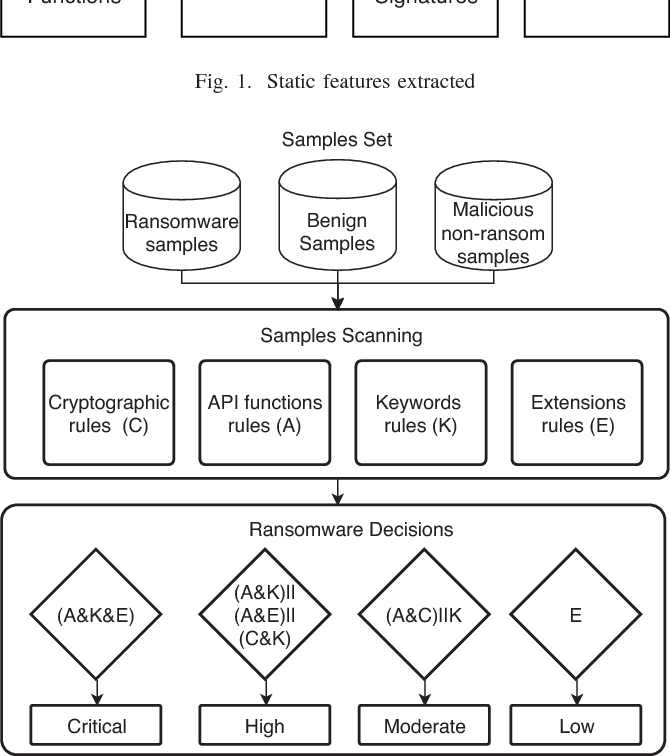
A new static-based framework for ransomware detection
Recently, ransomware attacks are on the rise hitting critical infrastructures and organizations globally. Ransomware uses advanced encryption techniques to encrypt important files on the targeted computer, then it requests payment to decrypt the encrypted files again. Therefore, the detection and prevention of ransomware attacks represent major challenges for security researchers. This research proposes a novel static-based rules ransomware detection framework. The decision rules of the proposed framework are based on static features extracted from the ransomware files. When scanned file
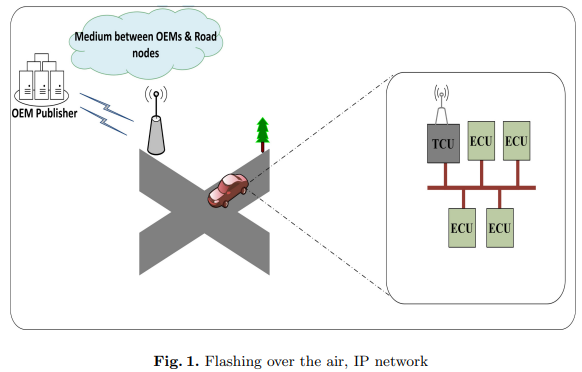
Vehicle Software Update over ICN Architectures
The Internet Protocol (IP) architecture could not fully satisfy Vehicular Ad-hoc Networks (VANETs) needed efficiency due to their dynamic topology and high mobility. This paper presents a technique to update the software of Electronic Control Units (ECUs) in vehicles using Information Centric Network (ICN) architecture. The proposed technique replaces Flashing Over The Air (FOTA) using IP with FOTA using ICN. The importance of FOTA is illustrated as well as the impact of applying the ICN architecture on VANETs. Through our experiments, we compare between the known FOTA over IP and the newly
Dyadchurn: Customer churn prediction using strong social ties
The increase in mobile phone subscriptions in recent years, has led to near market saturation in the telecom industry. As a result, it has become harder for telecom providers to acquire new customers, and the need for retaining existing ones has become of paramount importance. Because of fierce competition between different telecom providers and because the ease of which customers can move from one provider to another, all telecom service providers suffer from customer churn. In this paper, we propose a dyadic based churn prediction model, DyadChurn, where customer churn is modeled through
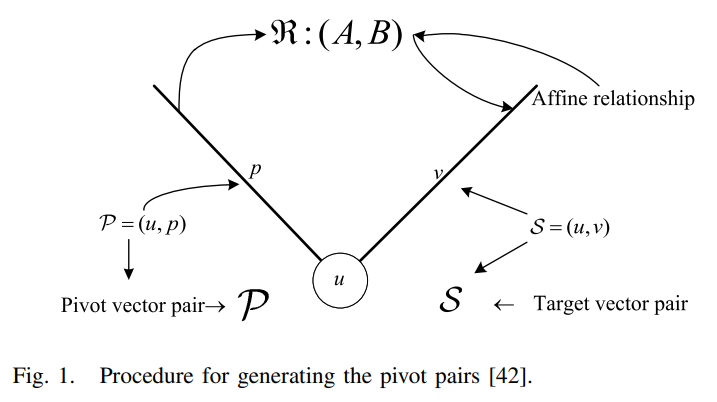
Dominant Data Set Selection Algorithms for Electricity Consumption Time-Series Data Analysis Based on Affine Transformation
In the explosive growth of time-series data (TSD), the scale of TSD suggests that the scale and capability of many Internet of Things (IoT)-based applications has already been exceeded. Moreover, redundancy persists in TSD due to the correlation between information acquired via different sources. In this article, we propose a cohort of dominant data set selection algorithms for electricity consumption TSD with a focus on discriminating the dominant data set that is a small data set but capable of representing the kernel information carried by TSD with an arbitrarily small error rate less than
Pagination
- Previous page ‹‹
- Page 18
- Next page ››
