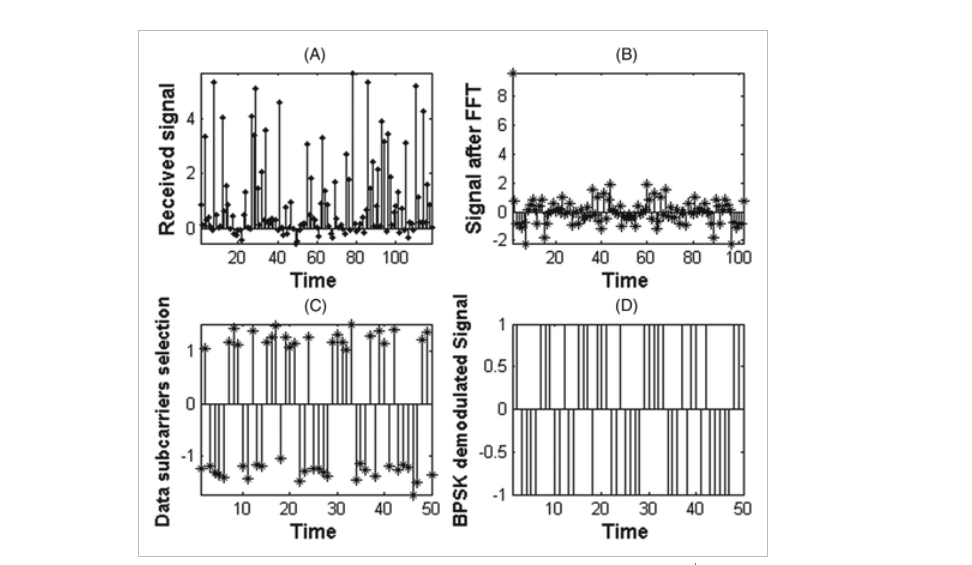
Odd clipping optical orthogonal frequency division multiplexing for VLC system
The Orthogonal Frequency Division Multiplexing (OFDM) has emerged as one of the promising techniques because of its robustness to multipath fading with high-speed data transmission. Classical bipolar OFDM cannot be used in intensity modulated with direct detection (IM/DD) optical communication systems, as visible light communication (VLC), so many optical modulation techniques as asymmetrical clipped optical OFDM (ACO-OFDM) and DC-Clipped OFDM (DCO-OFDM) have been investigated. In this paper, we introduce a novel optical modulation scheme that meets the optical communications requirements. The
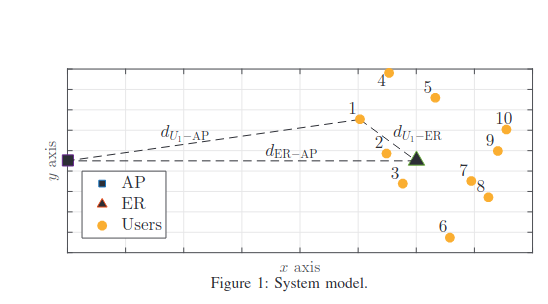
Non-Orthogonal Multiple Access schemes in Wireless Powered Communication Networks
We characterize time and power allocations to optimize the sum-throughput of a Wireless Powered Communication Network (WPCN) with Non-Orthogonal Multiple Access (NOMA). In our setup, an Energy Rich (ER) source broadcasts wireless energy to several devices, which use it to simultaneously transmit data to an Access Point (AP) on the uplink. Differently from most prior works, in this paper we consider a generic scenario, in which the ER and AP do not coincide, i.e., are two separate entities. We study two NOMA decoding schemes, namely Low Complexity Decoding (LCD) and Successive Interference
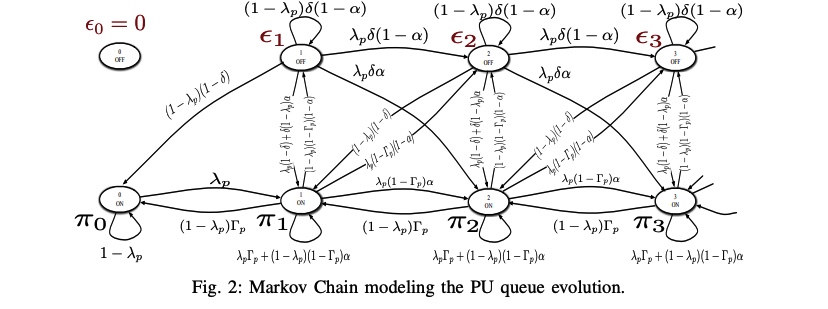
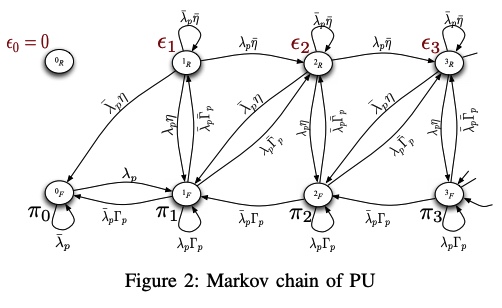
A feedback-soft sensing-based cognitive access scheme with feedback erasures
In this paper, we examine a cognitive spectrum access scheme in which a secondary user exploits the primary feedback information. We consider an overlay model in which the secondary user accesses the channel by certain access probabilities that are function of the spectrum sensing metric. In setting our problem, we assume that the secondary user can receive the primary link's feedback automatic repeat request (ARQ), but through an erasure channel. This means that the primary feedback may either be received correctly or is erased with a certain erasure probability. We study the cognitive radio
Full-duplex cooperative cognitive radio networks
In this paper, we study the impact of a full-duplex secondary node on a cognitive cooperative network with Multipacket Reception (MPR) capabilities at the receivers. Motivated by recent schemes that make full-duplex communication feasible, we study a model with one primary and one secondary transmitter-receiver pair, where the secondary transmitter is able to relay primary unsuccessful packets. Cooperation between primary and secondary users has been previously shown to be beneficial for the primary and the secondary users in terms of stable throughput. Our model assumes an imperfect full
A feedback-based access scheme for cognitive-relaying networks
In this paper, we consider a cognitive relaying network in which the secondary user accesses the channel with a certain access probability that depends on the feedback information sent by the primary destination. In addition, the secondary user is granted relaying capabilities by which it can relay primary traffic that was unsuccessfully transmitted by the primary user. We show that this proposed scheme enhances the performance of the secondary user as well as the primary user, while the QoS requirements of the primary user is unviolated. The secondary user can avoid sure collisions with the
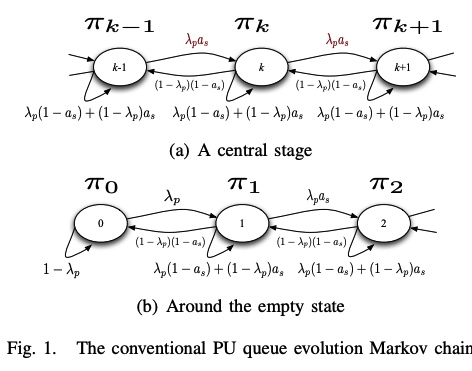
A feedback-based access scheme for cognitive radio systems
In this paper, we consider the design of access schemes for secondary users in cognitive radio systems based on the primary user feedback information. We consider a secondary user employing a random access scheme with an access probability that depends on the primary user feedback state. We show that the proposed scheme can enhance the system performance in terms of the secondary throughput and/or primary user delay while guaranteeing a certain quality of service (QoS) for the primary user; this is due to the fact that the proposed scheme avoids sure collisions between the primary and
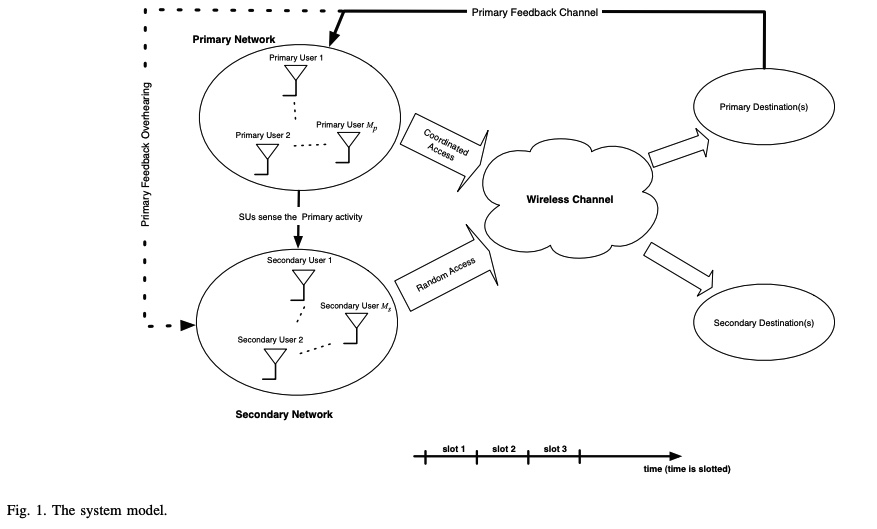
A feedback-soft sensing-based access scheme for cognitive radio networks
In this paper, we examine a cognitive spectrum access scheme in which secondary users exploit the primary feedback information. We consider an overlay secondary network employing a random access scheme in which secondary users access the channel by certain access probabilities that are functions of the spectrum sensing metric. In setting our problem, we assume that secondary users can eavesdrop on the primary link's feedback. We study the cognitive radio network from a queuing theory point of view. Access probabilities are determined by solving a secondary throughput maximization problem
Differential Evolution Mutations: Taxonomy, Comparison and Convergence Analysis
During last two decades, Differential Evolution (DE) proved to be one of the most popular and successful evolutionary algorithms for solving global optimization problems over continuous space. Proposing new mutation strategies to improve the optimization performance of (DE) is considered a significant research study. In DE, mutation operation plays a vital role in the performance of the algorithm. Therefore, in this paper, comprehensive analysis of the contributions on basic and novel mutation strategies that were proposed between 1995 and 2020 is presented. A new taxonomy based on the
Coagulation/flocculation process for textile mill effluent treatment: experimental and numerical perspectives
This study investigates the feasibility of applying coagulation/flocculation process for real textile wastewater treatment. Batch experiments were performed to detect the optimum performance of four different coagulants; Ferric Sulphate (Fe2(SO4)3), Aluminium Chloride (AlCl3), Aluminium Sulphate (Al2(SO4)3) and Ferric Chloride (FeCl3) at diverse ranges of pH (1–11) on the removal of chemical oxygen demand (COD), total suspended solids (TSS), colour, total nitrogen (TN) and turbidity from real textile wastewater. At pH 9, FeCl3 demonstrated the most effective removal for all studied
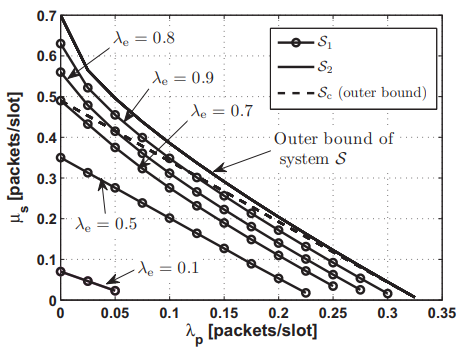
Maximum throughput of a cooperative energy harvesting cognitive radio user
In this paper, we investigate the maximum throughput of a saturated rechargeable secondary user (SU) sharing the spectrum with a primary user (PU). The SU harvests energy packets (tokens) from the environment with a certain harvesting rate. All transmitters are assumed to have data buffers. In addition to its own traffic buffer, the SU has a buffer for storing the admitted primary packets for relaying; and a buffer for storing the energy tokens harvested from the environment. We propose a new cooperative cognitive relaying protocol that allows the SU to relay a fraction of the undelivered
Pagination
- Previous page ‹‹
- Page 10
- Next page ››
