Remote Diagnosis, Maintenance and Prognosis for Advanced Driver Assistance Systems Using Machine Learning Algorithms
New challenges and complexities are continuously increasing in advanced driver assistance systems (ADAS) development (e.g. active safety, driver assistant and autonomous vehicle systems). Therefore, the health management of ADAS’ components needs special improvements. Since software contribution in ADAS’ development is increasing significantly, remote diagnosis and maintenance for ADAS become more important. Furthermore, it is highly recommended to predict the remaining useful life (RUL) for the prognosis of ADAS’ safety critical components; e.g. (Ultrasonic, Cameras, Radar, LIDAR). This paper
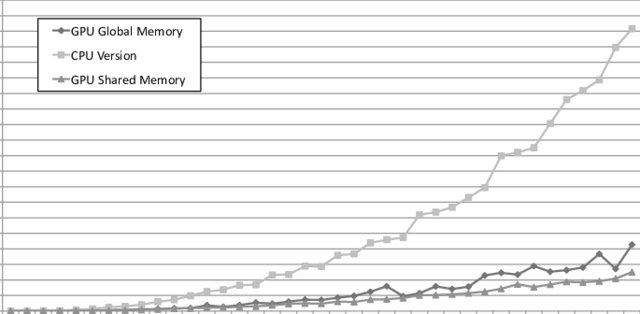
A GPU-enabled solver for time-constrained linear sum assignment problems
This paper deals with solving large instances of the Linear Sum Assignment Problems (LSAPs) under realtime constraints, using Graphical Processing Units (GPUs). The motivating scenario is an industrial application for P2P live streaming that is moderated by a central tracker that is periodically solving LSAP instances to optimize the connectivity of thousands of peers. However, our findings are generic enough to be applied in other contexts. Our main contribution is a parallel version of a heuristic algorithm called Deep Greedy Switching (DGS) on GPUs using the CUDA programming language. DGS
Tracking ground targets from a UAV using new P-N constraints
This paper presents improved automatic moving target detection and tracking framework that is suitable for UAV imagery. The framework is comprised of motion compensation phase to detect moving targets from a moving camera, target state estimation with Kalman filter, and overlap-rate-based data association. Finally, P-N learning is used to maintain target appearance by utilizing novel structural constraints to select positive and negative samples, where data association decisions are used as positive (P) constraints. After learning target appearance, a cascaded classifier is employed to detect
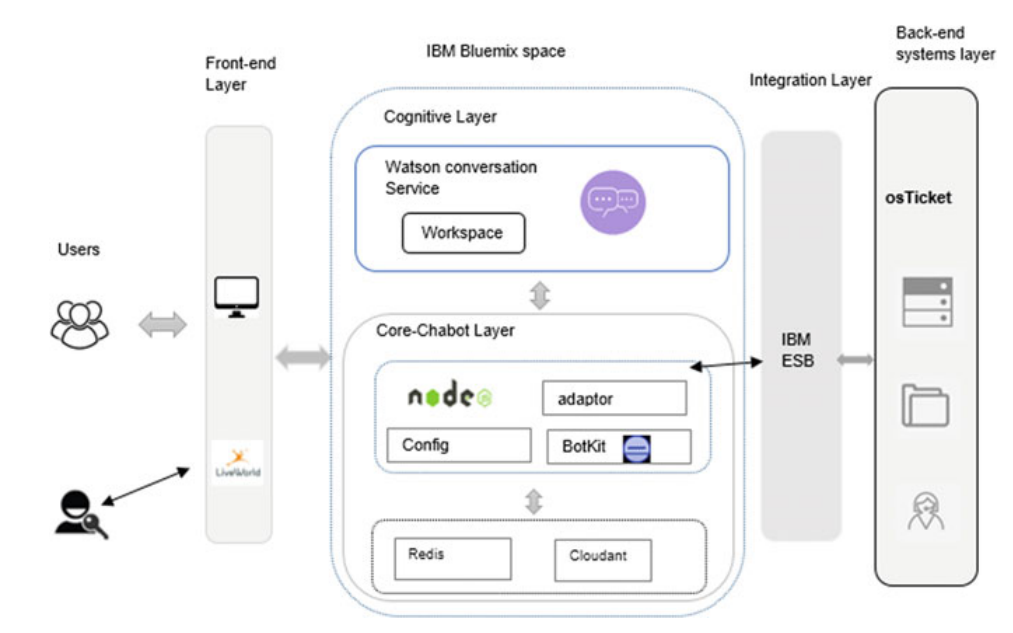
A study about using a cognitive agent in replacing level 1 and 2 service desk activities
The radical change in technology and high customer expectations and demand are pushing the service desk to provide a competent service for the customers. And this service should be faster, more flexible and gives a more accurate response and high user experience. Replacing the human call agent’s activities with a cognitive agent could improve the user experience by providing a faster response to customer’s requests, removing the human errors and giving 24/7 support with less operational cost. The cognitive agent has the potential to scale personalized and tailored interactions. And this will
Evaluation of Different Sarcasm Detection Models for Arabic News Headlines
Being sarcastic is to say something and to mean something else. Detecting sarcasm is key for social media analysis to differentiate between the two opposite polarities that an utterance may convey. Different techniques for detecting sarcasm are varying from rule-based models to Machine Learning and Deep Learning models. However, researchers tend to leverage Deep Learning in detecting sarcasm recently. On the other hand, the Arabic language has not witnessed much improvement in this research area. Bridging the gap in sarcasm detection of the Arabic language is the target behind this work. In
ANN-Python prediction model for the compressive strength of green concrete
Purpose: Utilization of sustainable materials is a global demand in the construction industry. Hence, this study aims to integrate waste management and artificial intelligence by developing an artificial neural network (ANN) model to predict the compressive strength of green concrete. The proposed model allows the use of recycled coarse aggregate (RCA), recycled fine aggregate (RFA) and fly ash (FA) as partial replacements of concrete constituents. Design/methodology/approach: The model is constructed, trained and validated using python through a set of experimental data collected from the
AutoDLCon: An Approach for Controlling the Automated Tuning for Deep Learning Networks
Neural networks have become the main building block on revolutionizing the field of artificial intelligence aided applications. With the wide availability of data and the increasing capacity of computing resources, they triggered a new era of state-of-the-art results in diverse directions. However, building neural network models is domain-specific, and figuring out the best architecture and hyper-parameters in each problem is still an art. In practice, it is a highly iterative process that is very time-consuming, requires substantial computing resources, and needs deep knowledge and solid
Transverse momentum spectra of strange hadrons within extensive and nonextensive statistics
Using generic (non)extensive statistics, in which the underlying system likely autonomously manifests its extensive and nonextensive statistical nature, we extract various fit parameters from the CMS experiment and compare these to the corresponding results obtained from Tsallis and Boltzmann statistics. The present study is designed to indicate the possible variations between the three types of statistical approaches and characterizes their dependence on collision energy, multiplicity, and size of the system of interest. We analyze the transverse momentum spectra pT of the strange hadrons Ks
Recognizing Clothing Patterns and Colors for BVI People Using Different Techniques
For blind and visually impaired (BVI) people, it is an arduous task to recognize clothing patterns and colors. It is especially complex to recognize them automatically. This is a highly researched area in image processing. This paper provides BVI with the ability to detect patterns and colors without depending on personal assistance, leading to increasing their confidence. The user first captures an image; then, our system detects colors and patterns. The color model used here is the hue saturation value (HSV). The main colors detected by our system are magenta, cyan, blue, green, red and
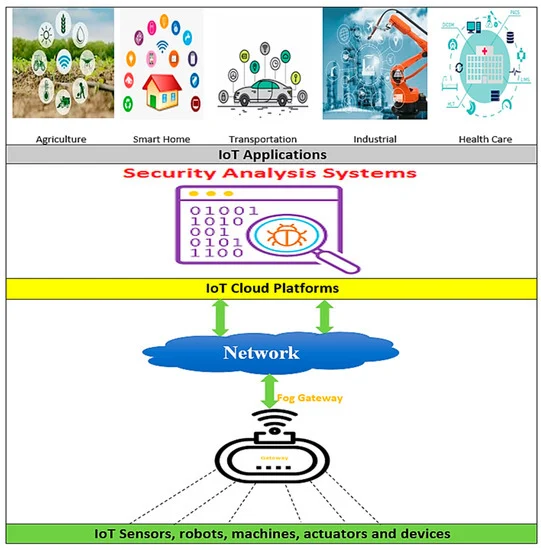
HSAS-MD Analyzer: A Hybrid Security Analysis System Using Model-Checking Technique and Deep Learning for Malware Detection in IoT Apps
Established Internet of Things (IoT) platforms suffer from their inability to determine whether an IoT app is secure or not. A security analysis system (SAS) is a protective shield against any attack that breaks down data privacy and security. Its main task focuses on detecting malware and verifying app behavior. There are many SASs implemented in various IoT applications. Most of them build on utilizing static or dynamic analysis separately. However, the hybrid analysis is the best for obtaining accurate results. The SAS provides an effective outcome according to many criteria related to the
Pagination
- Previous page ‹‹
- Page 18
- Next page ››
